Directory Traversal via ".tar" file
inspired by CTF Writeup
1. Concept
- Directory Traversal via .tar file
- CVE-2007-4559
- Bypass Patch code and advanced exploit
2. Exploit Principle before code was patched
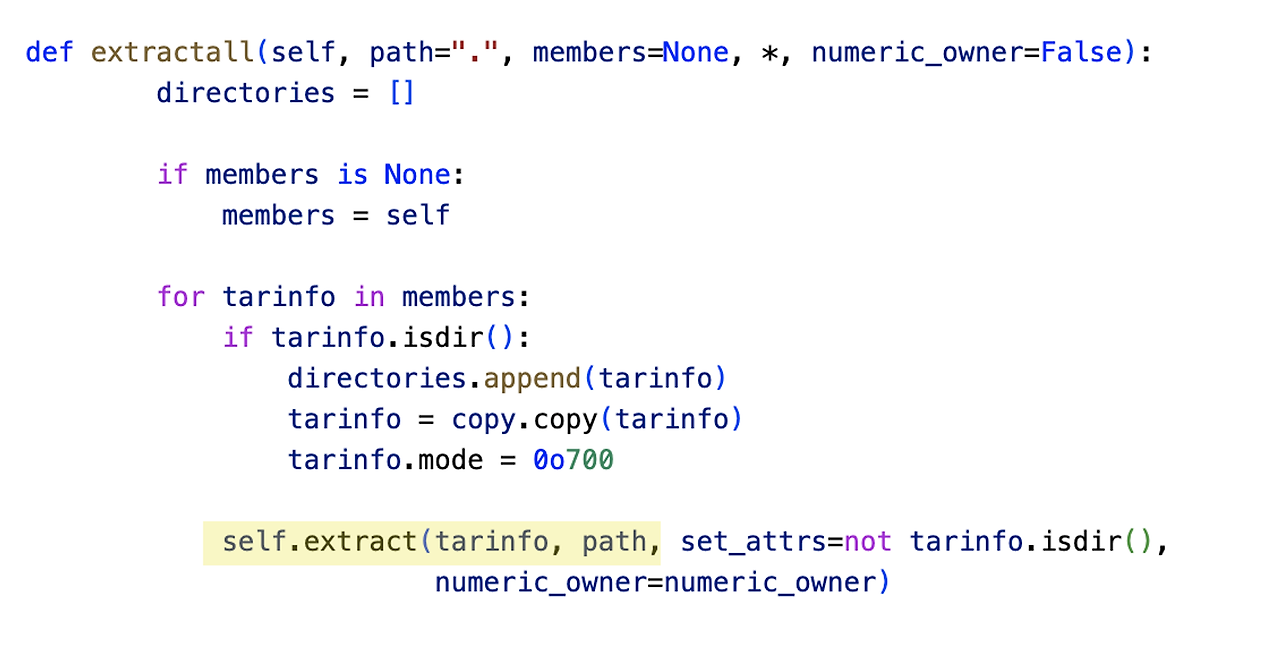
The vulnerability occurs when extracting files with the ”.tar” extension via the extract, extractall functions of the tarfile Python library.
When a file is saved, the filename is saved using the path and the tar filename.
1
2
e.g) path: ~/Desktop/ | filename : flag.tar
>> result: ~/Destkop/flag.tar
The extract and extractall functions extract specific files via a saved filename. But there is no validation of filename during the upload process. So attacker can upload the filename like “../../flag.tar”. If Web application has the functions of extracting and reading file contents, the attacker can read files in the parent directory.
3. Exploit principle after code was patched
I’m not sure this patch code is for preventing directory traversal vulnerability. Whatever, let’s check it out.
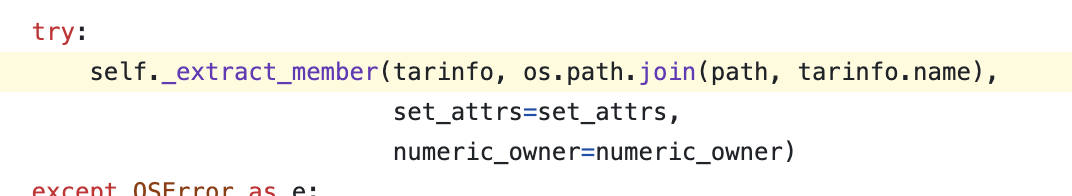
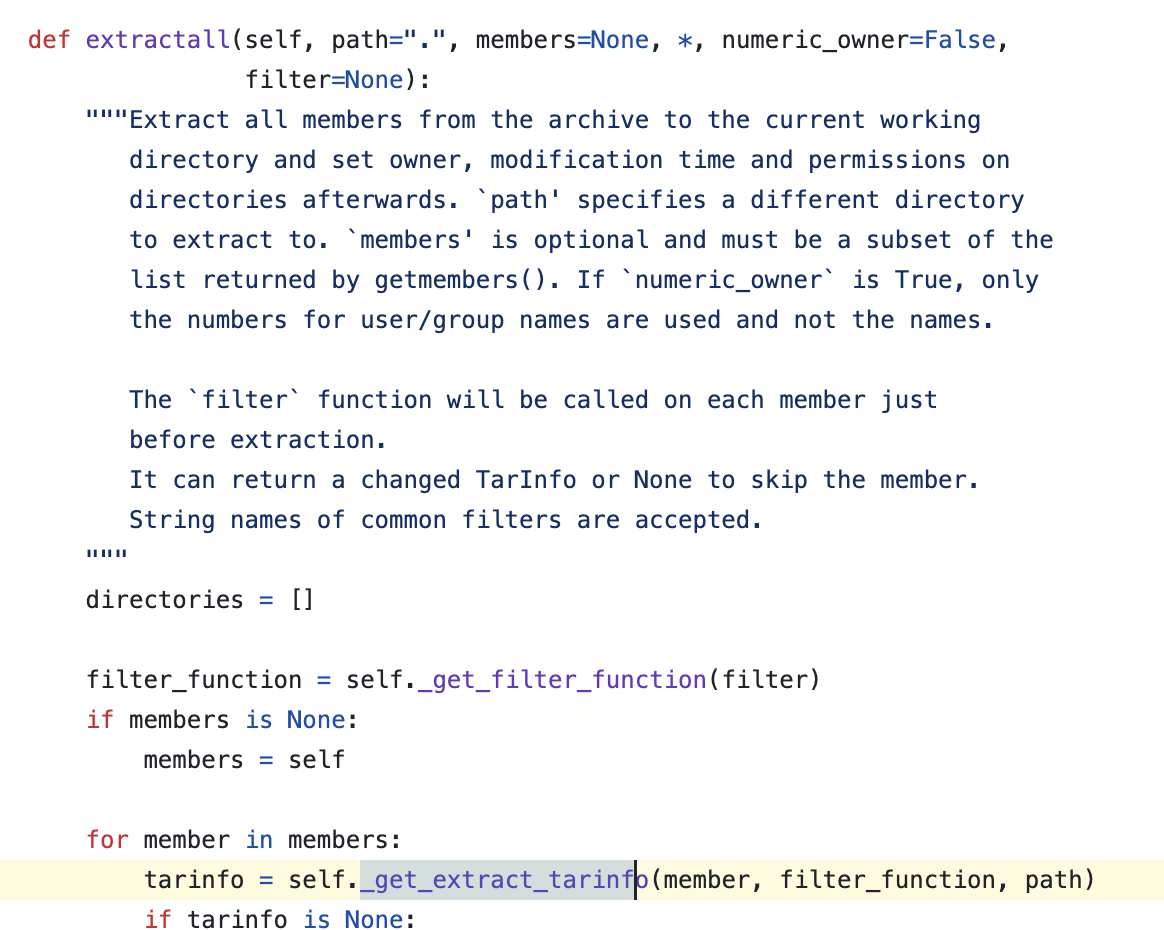
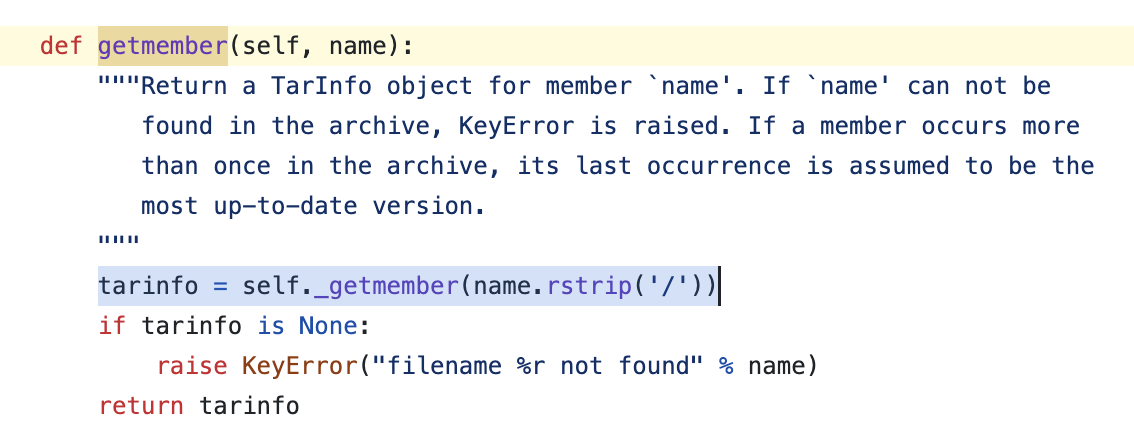
You can see _get_extract_tarinfo function is added recently.
Once inside, you can find the getmember function among the code related to filename.
When defining filename, specify the string from the first character before the slash as the filename. So we can’t exploit this with traditional method.
4. How to Bypass?
- We can’t directly input slash in filename
- To bypass this logic, use Symbolic link. Upload a zipped file that points to another file in the parent directory.
- If web application extracts the uploaded file and read it, the file points another file in the parent directory. Due to this process, the attacker can read other files.
5. Validation
This description simplifies the structure for better understanding. In real world, a web service should have the ability to upload a compressed file and ability to extract and display the compressed file to the user.
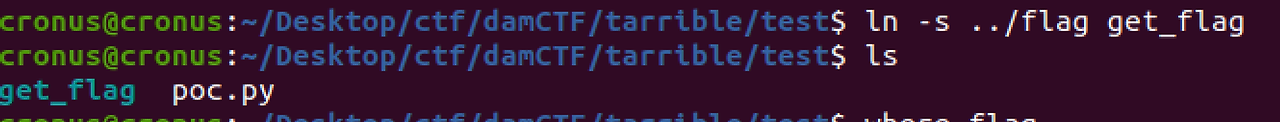
First, make a symoblic link file.
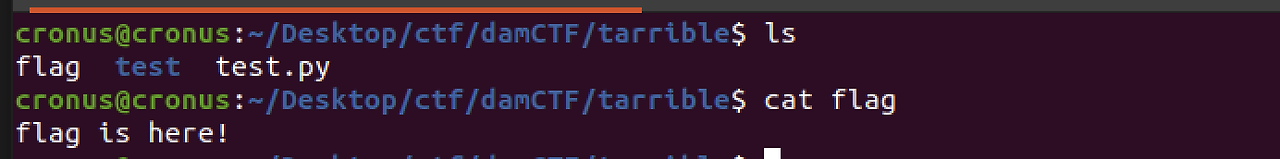
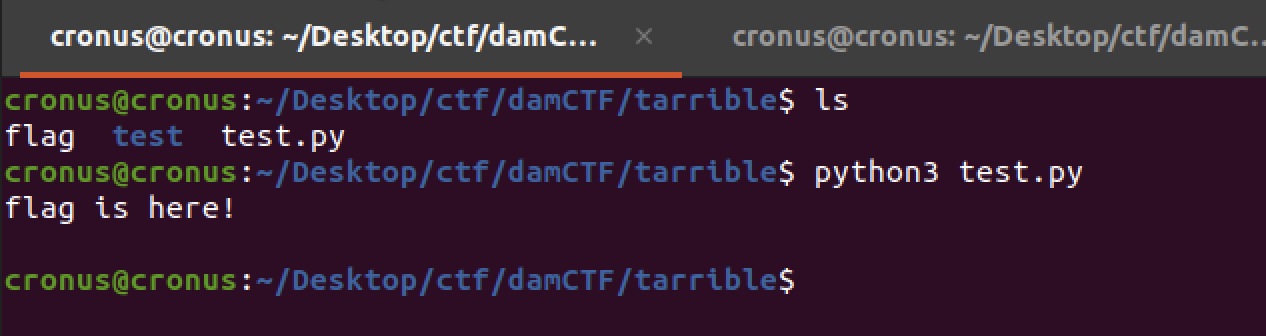
The flag file is in parent directory of test. ( relative path: ../ )
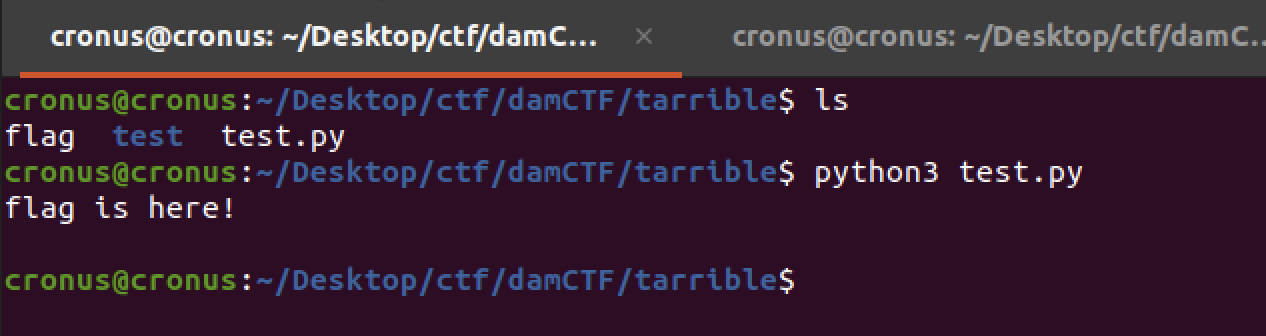
This is PoC Code. If run this code, flag file can be read.
• Side Note
- The above vulnerabilities exist not only in tar files, but also in popular compressed file formats (.zip, .jar, etc.)
- Not only Python(Flask, Django), but also NodeJS and Spring has this vulnerability.
- Mitigation : In my opinion, there are ways to strictly set access to directory folders to prevent access to parent directories.
( I googled mitigation, but there was nothing. So I write my private opinion :( )
Reference :
tarrible-storage : https://cronuse.tistory.com/283